Organizational Identity/Microsoft Accounts and Azure Active Directory – Part 2
In Part 1 of this blog we defined some key terms to help us now move into a deeper discussion of how to best integrate Azure Active Directory (AAD), Organizational Identities (OrgIDs), and Microsoft IDs. We defined Azure subscriptions and AAD tenants, then discussed the different types of administrative access for each entity. The goal of integrating all of these entities is to manage your Azure subscription(s) using only organizational accounts (as opposed to Microsoft accounts).
Within Part 2 of this blog we focus on specific use cases to accomplish this integration. We will look at different use cases related to existing Azure and AAD subscriptions to accomplish this. Each use case describes how to leverage the use of organizational accounts. To bring your Azure subscription under management of ONLY OrgIDs (no Microsoft accounts) follow the tasks outlined in the “Use Cases” section and then perform the following:
- Ensure that an organizational account identity which has co-administrator privileges within Azure can log in to the Azure Portal to manage his organization’s users in the environment.
- Remove the Microsoft accounts users from the being co-administrators. This may require a support call to move the Azure Service Subscription to a different co-administrator if the Azure Service administrator is a Microsoft account. In some cases you can also accomplish this from your subscription management UI.
Scope of Use Cases
The goal of these use cases are to bring your Azure subscription under management of ONLY organizational accounts (no Microsoft accounts). Items such as synchronization of on premise Active Directory to Azure Active Directory or the use of Active Directory Federation Services (ADFS) for single sign-on (SSO) between your on premise environment and your Azure Portal is outside the scope of this document.
Use Cases
- Case 1 – No existing AAD or Azure subscriptions
- Case 2 – Existing AAD tenant / no Azure subscription
- Case 3 – Existing Azure subscription / no AAD tenant
- Case 4 – Existing Azure subscription and existing AAD tenant
Case 1 – No Azure or AAD Subscriptions
In this situation there are no existing AAD or Azure subscription so we are starting from the beginning with respect to both of these. Here are two options to get started. Once you accomplish either or one of these you can go to one of the other three use cases.
- Option A (recommended): Use this link https://account.windowsazure.com/organization to sign up for Azure as an organization and get an AAD tenant in the process.
- Option B: Use this link http://www.windowsazure.com/en-us/pricing/free-trial/ to sign up for Azure with a personal account and get an AAD tenant later if you like.
Case 2 – Existing AAD Tenant / No Azure subscription
Your organization has an AAD tenant (that may be associated with an O365 subscription) but does not yet have an Azure subscription. You would like to sign-up for an Azure subscription and allow a select group of users in the AAD tenant to log on to the Azure Portal using their organizational accounts. Once subscribed to Azure your existing AAD tenant will automatically be accessible in the Azure Portal to a specified set of administrators.
An organization can use their OrgID credentials to login to Azure today and sign-up for their Azure trial subscription.
1. Subscribe to Azure by going to http://manage.windowsazure.com/
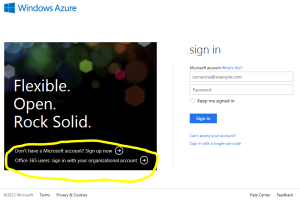
2. Log on using OrgID credentials by selecting the link circled in the above image and then entering your OrgID user id and password.
3. Select the link that is circled below to sign up for Windows Azure
4. Proceed through the sign-up process for your trial Azure subscription.
Key Point – Your AAD tenant will now be accessible automatically within the Azure Portal.
5. Additionally, you can add the OrgIDs (and Microsoft accounts) of the users you want to be co-administrators of your Azure subscription(s).
6. You may want to use the Azure Portal to register applications and/or add organizational accounts to the AAD tenant. The account(s) used to perform these tasks will need to have Global Administrator privileges for the AAD tenant.
Note: A co-administrator of the Azure Portal is not by themselves a Global Administrator of the AAD tenant. To administer the AAD tenant the user needs to be assigned the “Global Administrator” organizational role.
Case 3 – Existing Azure Subscription/ No AAD tenant
Your organization used a Microsoft account to set up their Azure subscription and does not have an AAD tenant. You would like to better manage the identities that administer the Azure subscription(s) via the Azure Portal by instantiating an AAD tenant. Since your organization started their Azure subscription(s) using Microsoft accounts, you can log into Azure Portal using the Microsoft account and get an AAD tenant.
Azure allows one AAD tenant per subscription. So when you create an AAD here you will enter all the OrgIDs you want to be a part of that AAD. Once an OrgID is part of an AAD, you can then make it a co-administrator in the Azure portal. You can then use that OrgID (instead of the Microsoft account used to originally create the Azure subscription) to log in to Azure and manage the AAD. If you want to delete the Microsoft account totally you can change this either by calling Azure support or doing it in account settings.
1. Log into Azure portal with Microsoft ID and click on Active Directory.
2. Add new users to the new AAD tenant. Use the OrgIDs of those users you would like to be co-administrators on your Azure subscription(s) and who are maintained in this new AAD tenant.
Note: You could also add Microsoft accounts to administer the AAD tenant. But the goal of this blog post is to get away from Microsoft account and use solely OrgIDs in the AAD tenant and login process.
3. When adding an Azure co-administrator assure that the correct subscription box is selected and the correct email address is entered.
If you would like integrate this Azure subscription with an AAD tenant created using an organizational account (perhaps in conjunction with O365) see the next case (Case 4).
Case 4 – Existing Azure Subscription / Existing AAD tenant
Your organization has an existing AAD tenant that was perhaps obtained via subscription to O365, Intune, CRM, etc. Your organization also has an existing Azure subscription, but it was created using a Microsoft account.
You would like a select group of users to use their OrgIDs to access the Azure Portal of the Azure subscription created using a Microsoft account. You also want the users to use their organizational accounts for registering applications and services in AAD.
1. Add the Azure account administrator’s Microsoft account to your AAD tenant.
Key Point – By adding an Azure account administrator to your AAD tenant this enables the Azure subscription to query the AAD tenant.
Hopefully the Azure account administrator is the same person as the Service Administrator. How do you tell if this is the case? You can use the Microsoft account in question and log in here with that account. https://account.windowsazure.com/Subscriptions. If you see the target Azure subscriptions listed you have the proper Microsoft account. If you do not see the target subscription or if you see the image below you do not have the proper account.
2. Log into the Azure portal at http://manage.windowsazure.com using an OrgID from your AAD tenant that has Global Administrator rights.
3. Log in using OrgID credentials by selecting the link circled in the above image and then entering your OrgID user id and password. If the AAD Global administrator does not have an Azure subscription, sign up for a free trial Azure subscription.
Note: This step is required so the AAD Global Administrator can access the AAD management interface. This step will be eliminated in the future.
4. Add the Azure account administrator’s Microsoft account (Live ID) to the AAD tenant. Make sure the user name field matches their Microsoft account.
5. If the Azure account administrator and the Azure Service Administrator are not the same then add the Azure Service administrator’s Microsoft Account to the AAD tenant as well.
6. Once the Azure account/Service administrator of the Azure subscription is in the AAD tenant that account can be used within Azure to add an organizational account from the AAD tenant to be a co-administrator on the Azure subscription.
Summary
In Part 2 of this blog we looked at four different combinations of how to use OrgIDs within both AAD and Azure subscriptions. There are various combinations you may have of existing Azure and AAD subscriptions that need to be handled slightly differently.
| User | User Experience in Azure Portal |
| Organizational account, Global Administrator | Sees AAD and can manage it |
| Organizational account, not Global Administrator | Does not see AAD in Azure portal |
| Microsoft account, Global Administrator | Sees AAD and can manage it |
| Microsoft account, not a member of a directory | Sees UX to create a directory |
The key to all this is the Account Administrator (AA) for your Azure subscription. That is the user that needs to be added to the AAD tenant so that tenant can be queried and is visible in the Azure AAD portal. Once the Account Administrator is part of the AAD tenant the Service Administrator (SA) can add other OrgIDs as Co-Administrators (CAs) to the Azure portal. The SA and CAs can then add OrgIDs to the AAD tenant in the Azure portal.
Best practices would suggest that the eventual owner of an Azure subscription should be the entity that is assigned/owns the Azure Account/Service Administrator role. For example, if an Azure development or test subscription is created for an organization it is highly recommended that the Azure Service Administrator role be assigned to an organizational account and not a Microsoft account. This will make the management of Co-Administrators within the subscription much easier during the life-cycle of the Azure subscription. You can also allow administrators from your AAD tenant to administer and manage your organizations users within Azure.
Here are some key links you can use to help you manage all this.
- To manage Azure subscriptions: https://account.windowsazure.com/Subscriptions
- To manage Azure, AAD, and organizational account: http://manage.windowsazure.com/
- To manage Microsoft account: https://account.live.com/
The preferred flow of this process is to obtain an Azure subscription, an AAD tenant, and an organizational account at https://account.windowsazure.com/organization. The end result of all this is that you can now use your organization’s AAD OrgIDs to log in and manage your Azure subscription and no longer need to use Microsoft IDs.