Aditi, my company, has just published a whitepaper I wrote (originally for MSDN) entitled “Maximizing SQL Server On Windows Azure IaaS”. To access the entire paper, go to http://www.aditi.com/Resources/Whitepaper/Maximizing-SQL-Server-On-Windows-Azure-IaaS/index.html and enter a few brief pieces of info about yourself to download the entire paper.
I have included the Introduction section here to give you an idea of what it includes.
Introduction
I have divided the content in this paper into two distinct parts to cater to both the neophyte and the initiated IT Professional in the Windows Azure IaaS VM environment. The purpose of the first section is to get past the initial hurdle of understanding the basics of installing and configuring SQL Server in Azure IaaS. It is targeted at the IT person who has very limited experience, if any, with SQL Server on a Windows Azure VM (Azure IaaS). The end result of this section is to get a single database up and running in the Azure Cloud. Once this baseline of knowledge is established, in the second section I will provide some advanced topics in the manner of best practices and recommendations to help optimize the performance and increase the availability of SQL Server on Azure IaaS. So if you already have a basic knowledge of SQL Server on IaaS VMs you can review section one or just skip it entirely and go to the advanced topics of the second section as there is not a dependency between the different sections.
The first section opens discussing how to configure and manage Azure disks and images. The Azure disks map to supplemental disks in Azure IaaS VMs and are used for the SQL Server data and log files. There are four primary choice for installing and configuring SQL Server in Azure IaaS to ensure you have a basic working configuration. For instance you can use an existing SQL Server image from the Azure VM Gallery. You can create a base Windows Server image and do a manual installation of SQL Server. You can forklift an existing VHD image with SQL Server already installed up into the Cloud. Or you can capture an existing Azure VM image containing SQL Server and use it as a base for additional SQL Server VMs. I will cover some very basic SQL Server administration done remotely over the public Internet including using the Azure portal and the third party AzureWatch tool for monitoring your installation.
Within the second section we examine some key advanced topics for optimizing SQL Server 2012 performance and availability on Azure IaaS. Topics include properly managing your VMs and disks. We see how to optimize SQL Server disk performance within Azure storage where we discuss optimizing IOPS (Input Output Operations/Second). We look at how to optimize the use of azure storage and provisioning of disks to maximize the performance of SQL Server on Windows Azure IaaS VMs. We’ll discuss Azure geo-replication of data and how it relates to multi-disk layouts and storage IOPs. We look into host caching for data and OS disks, how to format disks optimally for azure, managing lifetime of disks, and how to handle disks larger than 1 TB. We will look at how to utilize some Azure IaaS concepts such as affinity groups, virtual networks and their associated subnet, and best practices around VM connectivity to maximize the performance and minimize latency of SQL Server on Azure IaaS.
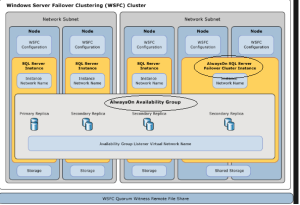
Also within the second section we will look at how to utilize Azure IaaS best practices to increase availability, performance, and locality of your SQL Server VMs. Specifically I am referring to ways better manage your SQL Server VMs and to synergistically provide optimal configuration management for more than one VM hosting SQL Server. For example, availability sets provide specialized VM failover protection in case SQL Server goes down. You can utilize some Azure IaaS concepts such as affinity groups, virtual networks and their associated subnets, and best practices around VM connectivity to maximize the performance of SQL Server on Windows Azure IaaS VMs. We will expand upon the simple Internet SQL Server administration model in the first section to show how best to secure remote administration leveraging the benefits of a virtual network. More than one SQL Server can share and accept incoming requests via balancing of the client load using shared endpoints. Using a combination of availability sets, load-balancing endpoints, and affinity groups helps ensure that your application is always available and running as fast and efficiently as possible. We will look at ways to replicate data across more than SQL Server VM. Specifically we will focus on SQL Server 2012 AlwaysOn Availability Groups and Listeners as the primary data replication choice. I will present some design recommendations that are key to correctly implementing configuration of SQL Server AlwaysOn Availability Groups. As a part of AlwaysOn we discuss and how to properly configure SQL Server VMs using Azure Availability Sets and Windows Server Failover Clustering (WSFC), SQL Server Availability Groups, and Availability Group Listeners to manage failover between VMs transparently.
I would like to note that this paper will not painstakingly step you through the steps of how to complete a SQL Server setup of SQL Server AlwaysOn Availability Groups or their associated Availability Groups Listeners. This is documented fully on MDSN in most cases. Rather, I will tell you how to do this in Azure and show you the end result of the steps needed to set these entities up. At the end I will provide a concise summary of the high-level steps to configure SQL Server AlwaysOn Availability Groups and Availability Groups Listeners within the Azure IaaS environment.
Throughout this document I will endeavor to add value via best practices and share experiences I have been through. That means I will provide links to as much existing content whenever possible to save space and not clutter the paper. This gives you information on the topic which we are discussing as well as additional contextual information to enhance your understanding. My goal is to keep this document as concise as possible giving you the main points and key recommendations and not to document processes or content that is already developed.